One of the dangers in today's online world is called cloning, often executed through clone phishing attacks. It's a sneaky method some criminals use to copy important stuff online and cause trouble.
In a recent News4JAX report, cybersecurity experts discussed the pressing issue of online privacy and data protection. Our own Tyler Chancey, Director of Scarlett Cybersecurity, was featured in this important discussion.
The threat of cyber-attacks has become a widespread concern. These attacks have become a significant threat frequently resulting in data breaches, service disruptions, and financial losses.
Live Nation has revealed that its Ticketmaster subsidiary experienced a data breach, with a hacker offering to sell customer data on the dark web, including names, addresses, phone numbers and some credit card details.
On Wednesday, May 8, 2024, Ascension, one of the largest nonprofit healthcare systems in the United States, fell victim to a suspected cyberattack, causing widespread disruption to clinical operations at its hospitals across the country.
Cyber threats are becoming more serious for people, businesses, and governments. Cyberattacks are powerful tools that cybercriminals use to break into computer systems. They steal private information, stop operations, and cause financial damage.
What is Malware Analysis?Malware analysis is the technique of assessing and understanding malicious software. This involves identifying the malware's form, objective, and capabilities, assessing how it grows and infects systems, and recognizing the…
In late January 2024, the City of Jacksonville Beach experienced major IT outages and disruptions to city systems and services. After weeks of investigating the "cybersecurity event", city officials announced on March 20th that they had been the…
Employees are crucial in protecting the company's sensitive information and assets. By following cybersecurity best practices, employees can reduce cyberattack risk and promote workplace safety.
Cybersecurity asset management is the process of finding, organizing, and managing an organization's digital assets to protect them from cyber threats.
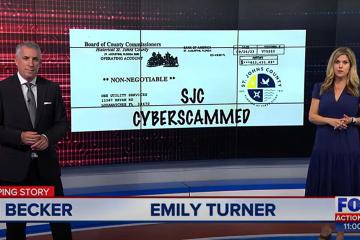
St. Johns County, Florida, worked to recover over $1 million lost to hackers through a business email scam.
Jacksonville Beach continued to grapple with computer issues following a cybersecurity event, with some functions still offline a week later. Tyler Chancey, Director of Cybersecurity for Scarlett Group, highlighted the increasing frequency of such…
Big data has become an important part of our everyday lives. Organizations of all kinds and fields are now collecting and analyzing huge amounts of data to learn more about their customers and make better decisions.
Phishing is one of the most significant cyber threats to individuals and organizations. Phishing is a technique that hackers use to trick people into giving them private information or doing things that could damage their security.
What is a Ransomware Attack?A ransomware attack is a type of malicious cyber attack in which the attacker encrypts victims’ data or sensitive information located on a computer system or device.
Jacksonville, FL – September 21, 2023: The Jacksonville Business Journal announced today that Scarlett Group is one of the 2023 Fast 50 honorees for the third year in a row.
ORANGE PARK, Florida — The Scarlett Group, a leading IT Services and Cybersecurity firm, stands among America’s fastest-growing private companies for a second year in a row.
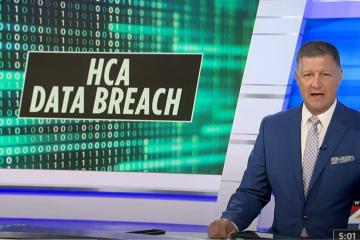
Stolen information from a data breach is causing millions of HCA Healthcare patients in Florida to worry. The company explained the private data was stolen from an external storage location used to automate email messages.
Annual MSP 501 Identifies Industry’s Best-in-Class Businesses
Growing Via Recurring Revenue and Innovation
JUNE 30, 2023: The Scarlett Group has been named one of the world’s premier managed service providers in the prestigious 2023 Channel Futures…
8 Critical Pros and Cons for AI Chatbots and IT
It’s rare to be able to easily identify an inflection point in tech. The winds of technological change can be subtle and undetected, slowly shifting the IT world around us without notice.